UTCTF 2020 - Chatt With Bratt
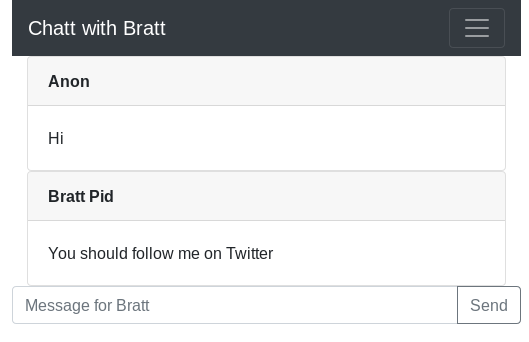
The application sets two cookies:
chat_id: UUID used to identify the chat log currently in use.secret: The one that potentially holds the flag on Bratt’s side.
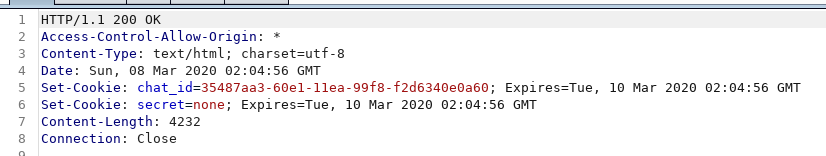
From this, we can assume that our goal is to get Bratt’s secret cookie.
My first thought was to exploit XSS. A quick smoke test on the application confirmed that it was vulnerable to XSS:

Now that I knew that triggering XSS was very simple, I tried using an XSS hunter payload and a little while later, we see that Bratt got hooked:

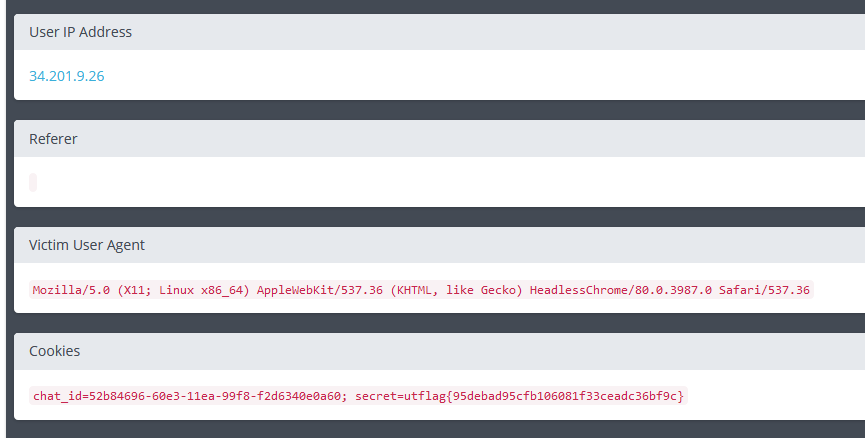
The flag was: utflag{95debad95cfb106081f33ceadc36bf9c}